If you happen to’ve ever shopped for hosting, you understand each supplier swears their safety is “rock strong.” Which sounds reassuring… till you understand “rock” can imply granite or it could actually imply ornamental backyard pebble.
The reality is, “safe internet hosting” can imply something from “we put in an SSL certificates as soon as” to “we have now a 24/7 safety operations middle scanning for threats you’ve by no means even heard of.” And except you understand what to search for, you may be paying for granite whereas really getting gravel.
When WordPress websites get compromised or hacked, it’s not often as a result of their homeowners are reckless. It’s as a result of their internet hosting safety is primary or lax when the enterprise ought to have upgraded to one thing extra strategic. So, as an alternative of simply questioning in case your internet hosting is safe (a query nearly each supplier will say sure to), the higher query is that this:
What stage of safety am I getting — and does it match the worth of my web site and my enterprise wants?
On this information, we’ll stroll you thru the WordPress Internet hosting Safety Maturity Mannequin, a five-stage framework that takes you from primary survival measures to bulletproof, business-aligned safety.
Determine the place you stand right now, what gaps you might be residing with, and whether or not your internet hosting is defending your development.
The Safety Maturity Actuality Examine
When a internet hosting firm says they’re safe, they most likely aren’t mendacity. They only won’t be telling you the entire story. It’s like when a restaurant menu says “locally-sourced.” Certain, the eggs got here from a farm 10 miles up the street. However the remainder of your dinner? Unloaded from a freezer truck.
That’s the issue with generic safety claims: with out context, they’re meaningless. SSL certificates, firewalls, backups —these are the baseline. They preserve your web site from collapsing underneath the obvious threats, however they don’t assure it’s protected towards the type of assaults that may carry your online business to its knees.
Why WordPress Internet hosting Safety Is Completely different
Not all internet hosting environments safe WordPress the identical approach. Generic internet hosting protects on the server stage, however WordPress-specific internet hosting bakes in protections tuned for the precise methods WordPress websites get attacked —plugins, themes, logins, and configuration information.
Right here’s how the 2 approaches examine:
| Function | Regular internet hosting | WordPress internet hosting (managed/specialised) |
| SSL & HTTPS | Often accessible, guide setup | Often included and auto-enabled |
| Firewall (WAF) | Generic guidelines for net assaults | Tuned for WordPress threats (login abuse, XML-RPC, plugin exploits) |
| Core/plugin updates | Handbook, user-managed | Typically auto-applied or prompted |
| Login safety | Generic brute-force safety | WP-specific (2FA, reCAPTCHA, price limiting on wp-login.php) |
| File hardening | Consumer-configured | Pre-configured (prohibit wp-config.php, disable dangerous capabilities) |
| Backups | Typically guide or at additional value | Automated each day backups with simple restore |
| Help | Basic internet hosting employees | WordPress-trained consultants |
The Hidden Prices of Being “Safe Sufficient”
Working under your safety wants can value you in the actual world.
- Downtime that kills gross sales: In a latest survey of 500 enterprise professionals, corporations reported shedding a median of 5 hours monthly to downtime. One in 5 mentioned they lose over $2,500 monthly due to it.
- Breaches that drag you down: Practically half of companies surveyed skilled hacking makes an attempt due to poor internet hosting safety, and 32% suffered precise information breaches.

Safety Is a Progress Enabler
Too many people deal with safety as a nuisance or a field to test. That’s short-sighted.
As a substitute, consider it as insurance coverage for development:
- Quick, dependable websites enhance web optimization rankings and preserve clients blissful.
- Stable compliance and information safety open doorways to new markets and contracts.
- If you’re assured that internet hosting has your again, you may give attention to scaling, not patching safety holes.
These aren’t simply technical wins; they’re enterprise strikes.
The 5-Stage Safety Maturity Mannequin: From Fundamental to Bulletproof
Web site safety isn’t a binary swap you flip on or off. It’s extra like a dimmer. On the lowest setting, you may nonetheless see what’s in entrance of you —however you will have room to show up the lights to see way more clearly.
The WordPress Internet hosting Safety Maturity Mannequin is our approach of turning the lights all the best way up. It helps you determine precisely the place your internet hosting stands right now, what threats you’re protected towards, and the place the gaps are hiding.
Every stage builds on the one earlier than it, beginning with bare-minimum survival options and climbing all the best way to military-grade defenses most small companies won’t ever really want (and shouldn’t pay for).
The aim is to match your internet hosting safety to your precise enterprise threat, so that you’re investing within the protections that make sense in your visitors, information, and development objectives.
Let’s begin on the backside rung and work our approach up.
Stage 1: Fundamental Safety

That is the “tenting in your yard with a flashlight” stage of internet hosting safety. You’ve obtained some gear —sufficient to get by means of a quiet night time —but when a storm hits or the raccoons get curious, you’re not precisely geared up to fend them off. At this stage, plugin and theme updates are completely guide. Many WordPress websites fall behind right here, leaving them open to exploits which have already been patched upstream.
At this stage, your host is providing you with absolutely the naked requirements:
- SSL/TLS encryption: That little padlock within the browser that claims your web site’s connection is safe. That is desk stakes; Google’s been favoring HTTPS websites for years.
- Fundamental backups: As soon as a day or so, and often saved proper on the identical server (which is like retaining your spare home key underneath the welcome mat).
- Shared internet hosting surroundings: Your web site probably lives on the identical server as dozens or tons of of others, sharing sources (and in some circumstances, vulnerabilities).
What It Protects You From
Stage 1 can protect you from informal drive-by threats, like information snooping over public Wi-Fi, guests getting “Web site Not Safe” warnings of their browser, and minor mishaps like by chance deleting a web page or two.
What It Doesn’t Shield You From
Something focused, persistent, or automated. A brute-force login assault? A susceptible plugin exploit? A spike in visitors that crashes your server? At Stage 1, you’re mainly hoping these issues don’t occur to you.
Who It’s For
If you happen to’re operating a private weblog, a static brochure web site for a neighborhood membership, otherwise you’re simply dipping your toes into WordPress with minimal visitors and nil e-commerce, Stage 1 may be tremendous…for now.
The Hidden Price of Staying Right here
Ready till one thing occurs to improve your safety is a chance. When you begin accumulating buyer information, promoting merchandise, or getting common visitors, you’ve outgrown Stage 1. And in the event you don’t transfer up the ladder, you might end up cleansing up a large number that prices greater than a yr of higher internet hosting.
Questions To Ask Your Host:
- How usually are backups taken, and the place are they saved?
- Is SSL included and mechanically renewed?
- How shortly can I restore my web site from a backup if one thing goes unsuitable?
If their solutions are fuzzy (or contain additional charges for fundamentals), you’re trying on the minimal attainable funding in safety. That’s tremendous for a passion web site, however not for a enterprise you really need to develop.
Stage 2: Proactive Protection

If Stage 1 is tenting in your yard with a flashlight, Stage 2 is not less than checking the climate forecast earlier than you pitch the tent. You’re placing up some defenses to maintain bother from reaching you within the first place.
At this stage, your host must be offering instruments that actively monitor and block frequent threats, not simply clear up after them.
- Net Utility Firewall (WAF): Filters malicious visitors earlier than it reaches your web site. WAF blocks frequent assaults, like SQL injection and cross-site scripting. A WAF tuned for WordPress blocks frequent vectors like XML-RPC abuse, brute-force makes an attempt on wp-login.php, and identified plugin exploit signatures — issues generic firewalls would possibly miss.
- Automated malware scanning: Common sweeps that search for malicious code hiding in your information.
- Brute-force safety: Login try limits or two-factor authentication to maintain automated bots from hammering your login web page.
- Fundamental efficiency monitoring: Alerts for downtime or uncommon visitors spikes so you may react shortly
What It Protects You From
Stage 2 helps fend off opportunistic hackers, automated botnets, and the extra apparent plugin vulnerabilities that attackers scan the web for. It additionally buys you time. If one thing suspicious pops up, you’ll hear about it earlier than it spirals into a significant incident.
What It Doesn’t Shield You From
Superior, focused assaults. At Stage 2, your defenses are nonetheless largely “off the shelf,” which suggests decided attackers can discover methods round them. There’s additionally restricted isolation between your web site and others on the identical server, so a breach elsewhere might, in uncommon circumstances, spill over.
Who It’s For
Small to medium-sized companies with energetic content material updates, modest e-commerce exercise, or rising mailing lists. If you happen to’re accumulating any buyer information (even simply emails), you ought to be not less than right here.
The Hidden Price of Staying Right here
You’re protected towards the low-hanging fruit attackers go after first, however the extra useful your web site turns into, the larger the goal in your again. Staying at Stage 2 too lengthy is like locking your entrance door however leaving the home windows open.
Questions To Ask Your Host:
- How is your WAF configured, and is it up to date mechanically?
- How usually do you scan for malware, and what occurs in the event you discover some?
- Do you restrict login makes an attempt or supply 2FA?
Stage 3: Superior Safety

If Stage 2 is locking your doorways and setting an alarm, Stage 3 is hiring a safety guard who really is aware of how one can spot bother earlier than it begins. At this stage, your internet hosting is actively isolating, monitoring, and adapting to cease new ones of their tracks.
- Superior menace detection: Fixed scanning that doesn’t simply search for identified malware signatures, but in addition suspicious habits patterns.
- Account and course of isolation: Every web site or account on the server is walled off so a breach in a single can’t spill into one other.
- DDoS safety: Defenses towards huge floods of visitors meant to overwhelm your web site.
- Staging environments: Allow you to safely take a look at updates and modifications earlier than pushing them stay, lowering the danger of breaking your web site or introducing vulnerabilities. Staging environments are particularly vital for WordPress. With so many plugins and themes interacting, updates can break your web site in the event you don’t take a look at them in a sandbox first.
- Extra frequent backups, saved off-server: If one thing does go unsuitable, you may restore from a clear backup that isn’t sitting proper subsequent to the issue.
What It Protects You From
Stage 3 stops most opportunistic and lots of focused assaults. Botnets, large-scale automated intrusion makes an attempt, and cross-site contamination are a lot much less more likely to get by means of. You additionally acquire resilience towards performance-related assaults, like DDoS floods that may take down unprotected websites.
What It Doesn’t Shield You From
Extremely specialised assaults aimed instantly at your online business, or threats that require enterprise-level compliance and monitoring. This can be a sturdy center floor, however it’s not designed for organizations coping with regulated information or state-level menace actors.
Who It’s For
Income-critical web sites, like thriving e-commerce shops, membership platforms, businesses internet hosting a number of shopper websites, or any enterprise the place downtime means shedding actual cash and belief.
The Hidden Price of Staying Right here
Stage 3 can really feel “adequate” for a very long time, and for a lot of companies, it’s. However in the event you broaden into regulated markets, begin dealing with extra delicate buyer information, or expertise speedy development, the gaps between Stage 3 and enterprise-grade safety begin to matter.
Questions To Ask Your Host:
- Do you isolate accounts on the server stage?
- How shortly are you able to mitigate a DDoS assault?
- Are backups saved offsite and encrypted?
- Can I create a staging surroundings for testing?
Stage 4: Enterprise-Grade
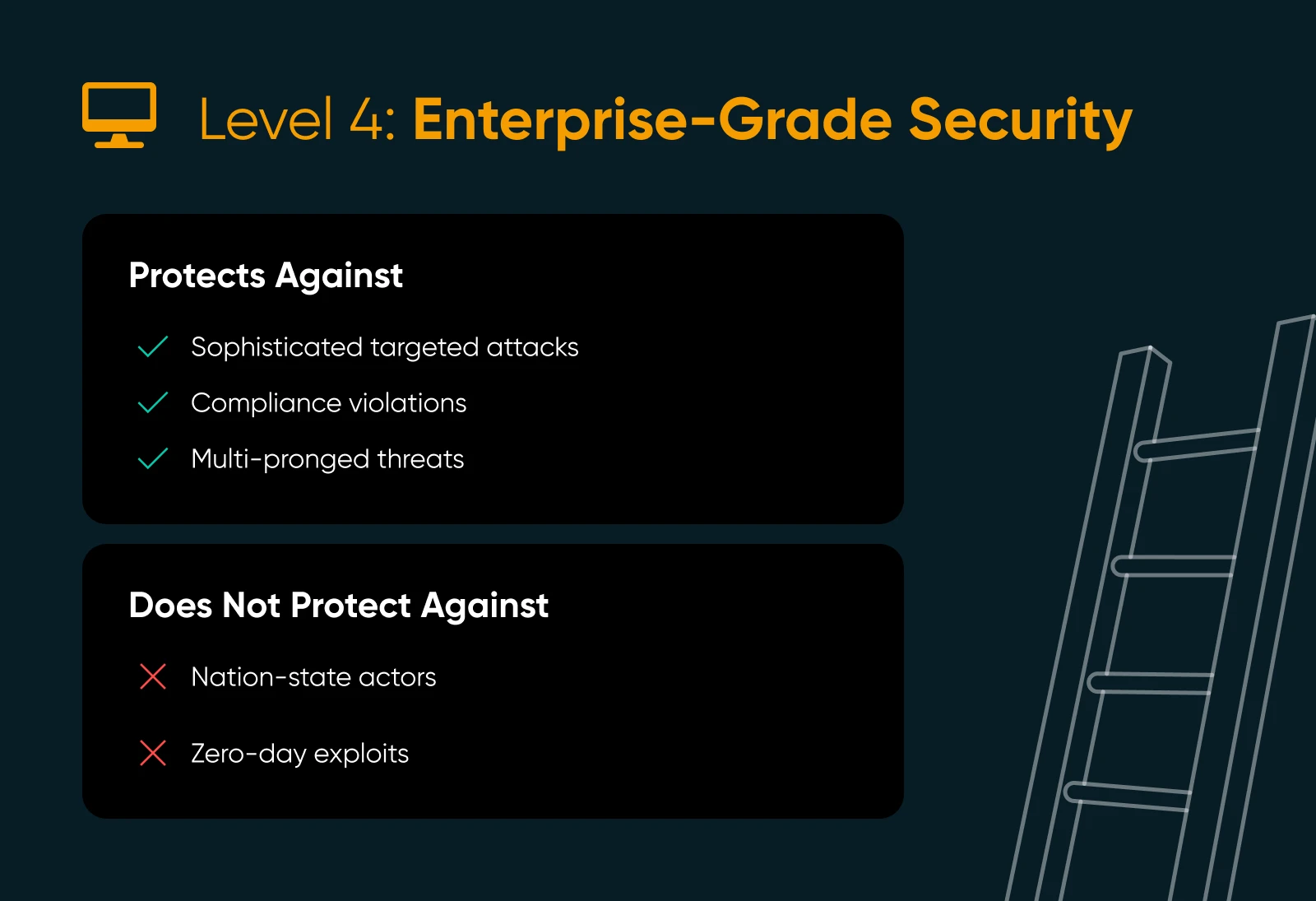
At this level, you’ve moved from having a succesful safety guard to operating your individual 24/7 command middle. Stage 4 is about technique —not simply stopping assaults, however anticipating them, assembly strict compliance necessities, and proving you’ve carried out it.
- Safety Operations Middle (SOC) monitoring: Round-the-clock human oversight, backed by superior tooling to identify and reply to incidents in actual time.
- Compliance-ready infrastructure: Help for trade requirements like PCI DSS (for bank card information) or GDPR (for private information safety), with clear documentation. Compliance issues most for WordPress ecommerce or membership websites. If you happen to’re operating WooCommerce and processing bank cards or storing private information, enterprise-level safety may also help you meet PCI DSS and GDPR necessities.
- Superior logging and audit trails: Complete information of consumer exercise and server occasions for safety critiques and forensic investigations.
- Customizable safety guidelines: The flexibility to tailor firewall and monitoring configurations to your particular threat profile.
What It Protects You From
Subtle focused assaults, compliance violations, and the type of multi-pronged threats that may cripple a enterprise with out correct oversight. Stage 4 offers you the receipts to show you’re safe to regulators, companions, and clients.
What It Doesn’t Shield You From
Nation-state actors or essentially the most cutting-edge zero-day exploits. Stage 4 is extraordinarily sturdy, however there’s nonetheless a ultimate tier for organizations with the best stakes.
Who It’s For
Established e-commerce manufacturers, SaaS corporations, monetary service suppliers, healthcare organizations, or anybody who should meet compliance necessities whereas sustaining uninterrupted service.
The Hidden Price of Staying Right here
If you happen to actually function in a high-risk, high-value surroundings (suppose confidential R&D information or authorities contracts), even Stage 4’s complete defenses would possibly depart a small however vital hole.
Questions To Ask Your Host:
- Do you present compliance documentation and help?
- What’s your course of for real-time incident response?
- How lengthy are logs retained, and are they tamper-proof?
Stage 5: Navy-Grade, Bulletproof Safety

That is the digital equal of a fortified bunker with biometric locks, armed guards, and an air filtration system that might survive the apocalypse. Whereas most small companies won’t ever want Stage 5, giant WordPress multisite networks or authorities/finance organizations operating WP functions generally require zero-trust and AI-driven defenses. This stage gives:
- Zero-trust structure: Each consumer, gadget, and connection should confirm itself at each step, no exceptions.
- AI-driven menace detection: Machine studying fashions flag anomalies in actual time, catching even brand-new assault strategies.
- Customized, client-specific safety infrastructure: Devoted servers, totally remoted environments, and bespoke firewall guidelines.
- Steady penetration testing: Common, simulated assaults to seek out weaknesses earlier than actual attackers do.
What It Protects You From
Virtually all the things wanting somebody bodily strolling into your information middle with dangerous intentions. This stage is designed to face up to superior persistent threats, subtle zero-day exploits, and essentially the most resourceful adversaries.
What It Doesn’t Shield You From
Human error. Even essentially the most superior programs can’t prevent if somebody uploads malware disguised as a spreadsheet or offers away credentials in a phishing rip-off.
Who It’s For
Authorities businesses, protection contractors, multinational companies in regulated industries, or corporations dealing with extraordinarily delicate mental property.
The Hidden Price of Staying Right here
Sarcastically, over-securing your internet hosting will be as inefficient as under-securing it. Stage 5 safety is dear and sophisticated, so in the event you don’t want it, you’re burning capital you might make investments elsewhere in your online business.
Questions To Ask Your Host:
- Do you assist zero-trust community segmentation?
- Can AI fashions be tailor-made to my particular surroundings?
- How usually are penetration exams carried out, and who conducts them?
Your Safety Maturity Motion Plan
Now that you understand the 5 ranges, it’s time to determine the place you are — and whether or not that’s adequate for your online business right now (and tomorrow).
Observe this four-step motion plan to seek out out.
Step 1: Self Evaluation
Ask your self:
- What safety features does my host present on the server stage?
- How shortly would I do know if considered one of my plugins launched a vulnerability?
- How briskly might I get better from an entire web site wipe?
- Can I restore my complete WordPress web site — core, plugins, themes, database, media — in a single click on?
If you happen to’re uncertain about any of those solutions, your safety maturity stage might be decrease than you suppose.
Step 2: Hole Evaluation
Match your present stage to the threats it doesn’t cowl. For instance:
- At Stage 1, you’re uncovered to brute-force assaults and malware.
- At Stage 2, you continue to lack isolation and superior menace detection.
- At Stage 3, you’re lacking compliance instruments and customized safety guidelines.
Figuring out your gaps helps you to determine whether or not you’re accepting these dangers or prepared to shut them.
Step 3: Improve Roadmap
Transitioning from Stage 1 to Stage 4 in a single day will be costly and overwhelming. As a substitute, give attention to the subsequent logical step.
If you happen to’re on primary shared internet hosting, begin by including a WAF and automatic malware scans to get to Stage 2. If you happen to’re already there, push for account isolation and DDoS safety to get to Stage 3.
Step 4: ROI Examine
Does the funding make sense for your online business? If higher safety prevents even one main outage or breach, the associated fee usually pays for itself many instances over. For instance, spending $50 a month on upgraded internet hosting to keep away from a $2,500 downtime loss isn’t an expense — it’s insurance coverage that earns its preserve.
From Survival Mode to Strategic Safety
Your internet hosting safety maturity stage is a enterprise choice. Working a heavy-traffic retailer on Stage 1 is like parking your Ferrari in a sketchy alley. Then again, paying for Stage 5 once you run a small native weblog is like hiring the Secret Service to observe your backyard shed.
The candy spot is discovering the extent that protects your income, repute, and development with out overspending on options you’ll by no means use.
At DreamHost, we construct safety into each layer of our WordPress internet hosting, from free SSL and automatic updates to each day backups, malware scanning, and WordPress-trained assist. Discover DreamHost WordPress internet hosting, discover your good match, and provides your web site the safety it must develop with confidence.

Shield Your Web site with DreamShield
Our premium safety add-on scans your web site weekly to make sure it is freed from malicious code.
Did you get pleasure from this text?









