Digital advertising and marketing strikes quick, and that tempo makes safety straightforward to miss. But each marketing campaign depends on secure websites, intact analytics, and guarded consumer information. A robust strategy to cyber safety in digital advertising and marketing helps companies work confidently as they launch new campaigns, add integrations, and handle high-traffic moments. When safety turns into a part of your on a regular basis workflow, you safeguard consumer belief and hold your advertising and marketing efficiency on monitor.
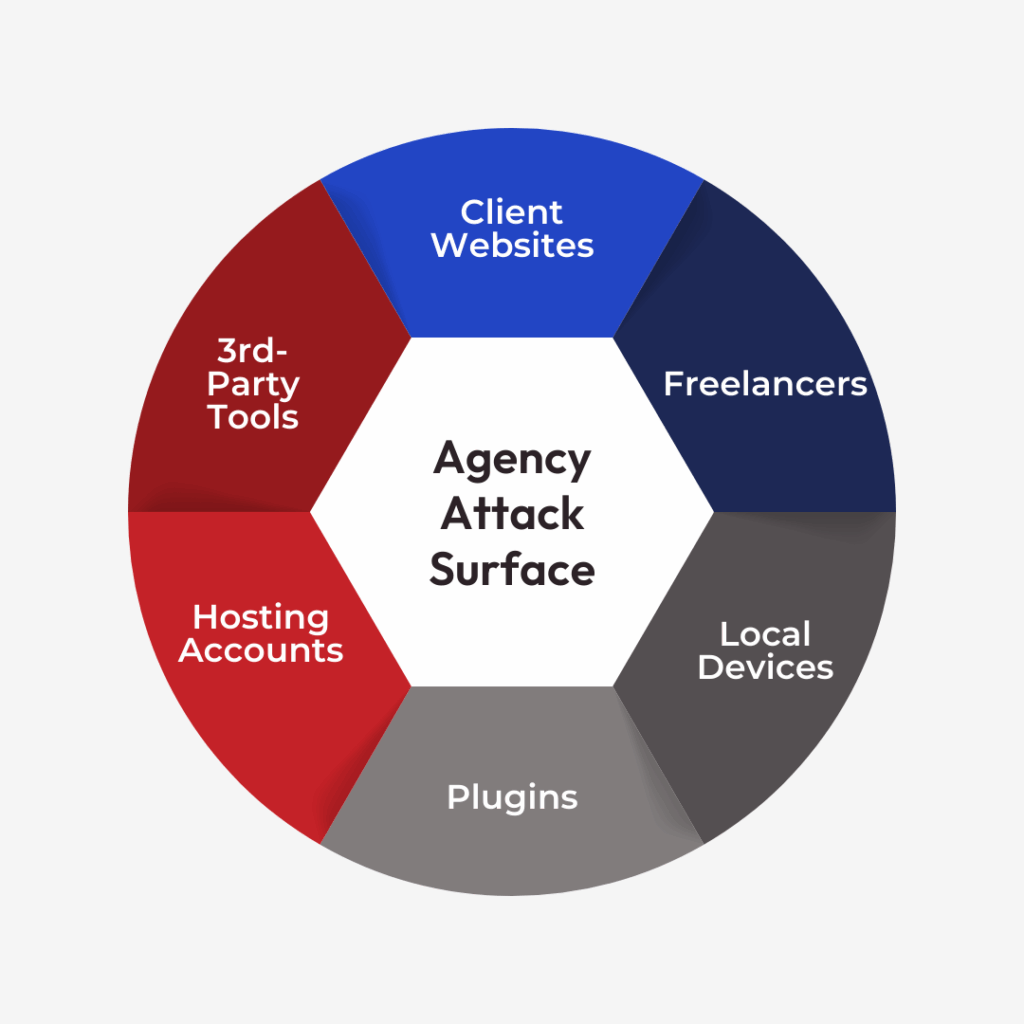
Whenever you handle a number of consumer websites as a advertising and marketing company, you carry extra safety threat than a typical website proprietor. Marketing campaign microsites, touchdown pages, lead-gen varieties, and monitoring scripts all increase your assault floor.
Safety isn’t only a technical checkbox: it’s tied on to your reliability, consumer relationships, and fame. When shoppers spend money on campaigns, promoting spend, and long-term model fairness, they count on their websites to remain safe. In line with IBM’s 2024 Price of a Knowledge Breach Report, the typical information breach now prices $4.88 million: a stark reminder that safety failures carry actual monetary penalties. When shoppers spend money on campaigns, promoting spend, and long-term model fairness, they count on their websites and advertising and marketing information to remain safe.
This information covers the core safety rules each company ought to perceive and implement, supported by confirmed practices for WordPress, Joomla, and custom-coded websites.
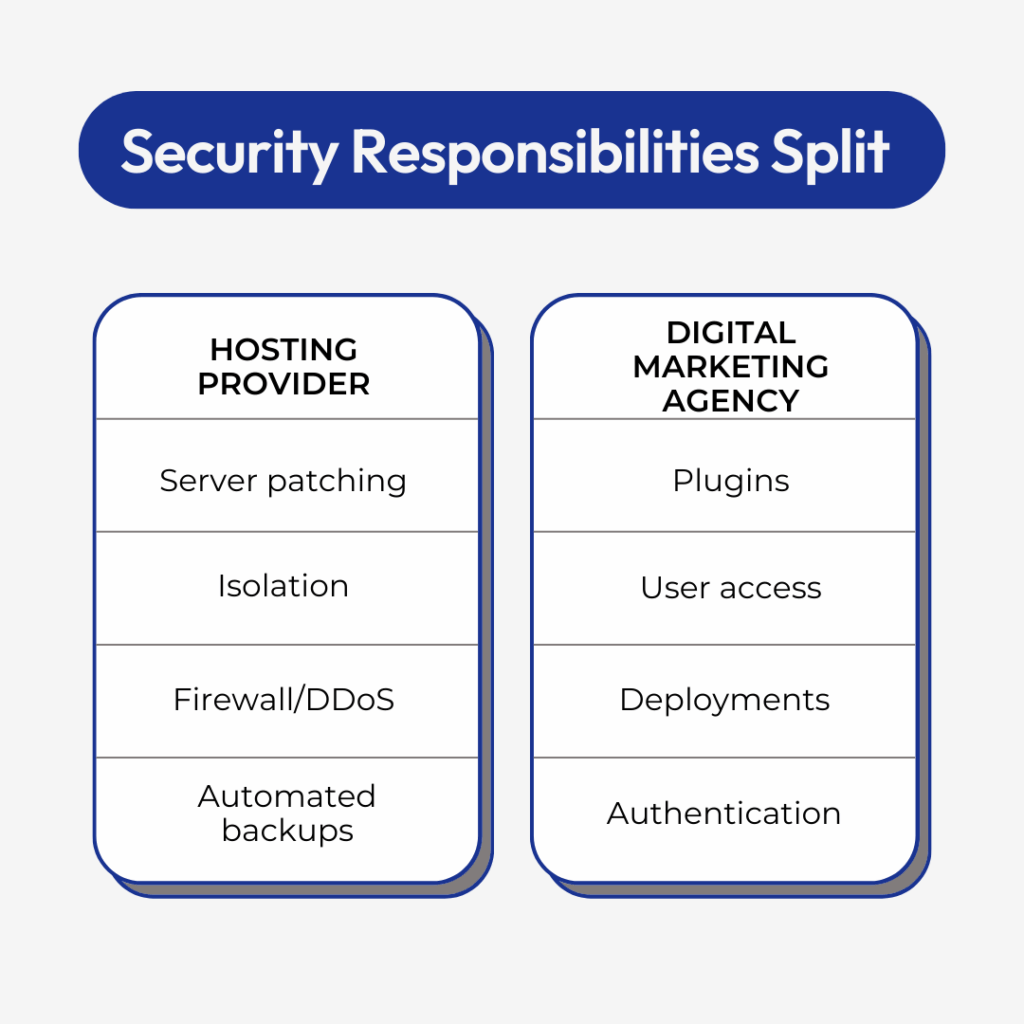
Safety Is a Shared Duty
Your internet hosting platform supplies the inspiration: remoted accounts, fashionable PHP variations, hardened server settings, and automatic patching. However you’re liable for the appliance layer: the place plugins, themes, credentials, and deployments occur each day.
Preserve Software program Up to date
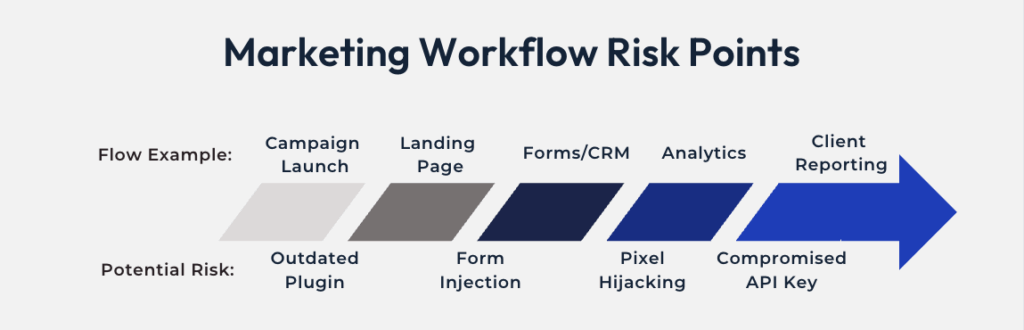
Each outdated plugin introduces threat. Attackers scan for publicly accessible code vulnerabilities in open-source CMSs. Most compromises happen as a result of software program isn’t up to date persistently. The window between a vulnerability disclosure and lively exploitation may be simply hours. Analysis from Patchstack exhibits that 7,966 new WordPress vulnerabilities have been found in 2024 alone. That’s a 34% improve from the earlier yr.
WordPress internet hosting, Joomla, and comparable platforms launch frequent updates that always embrace pressing safety patches. Whenever you handle dozens of websites, a missed replace can stay unnoticed for months whereas attackers actively exploit that actual vulnerability. This creates a silent safety debt that compounds throughout your whole consumer portfolio. The WPScan vulnerability database tracks over 64,000 vulnerabilities within the WordPress ecosystem, with 97% originating from plugins moderately than WordPress core.
Your replace technique ought to embrace:
- Computerized core updates when potential
- Weekly plugin and theme replace checks
- Fast patching for crucial safety releases
- Testing updates in staging earlier than manufacturing deployment
Implement Robust Authentication
Multi-factor authentication (MFA) is likely one of the easiest and simplest strategies to stop unauthorized entry. Mixed with password managers and complexity necessities, MFA dramatically reduces your threat profile. Even when a password is compromised via phishing or information breaches, MFA supplies a crucial second barrier. Credential-based assaults at the moment are the most typical preliminary assault vector, accounting for 16% of all breaches and taking a mean of 292 days to establish and comprise. cPanel’s security measures embrace built-in two-factor authentication choices.
Keep away from shared logins for non permanent contractors. A single shared credential usually turns into the foundation reason behind main safety incidents. When a number of individuals use the identical login, you lose accountability and create alternatives for credential leakage.
Management Entry All through the Lifecycle
Entry sprawl is likely one of the largest safety gaps companies face. Former workers, freelancers, and non permanent companions usually retain credentials lengthy after initiatives finish. Whereas they might not act maliciously, their native machines, saved passwords, or compromised e mail accounts can change into assault vectors.
Implement a structured entry lifecycle:
- Grant least-privilege entry for every position
- Revoke all credentials when initiatives shut
- Doc each login, permission, and integration
- Audit person lists month-to-month
Monitor Deployments and File Modifications
You possibly can’t shield what you possibly can’t observe. Observe theme edits, plugin installations, core updates, and new integrations. Attackers usually cover inside reputable recordsdata or quietly add backdoors. Monitoring supplies the visibility you should detect issues earlier than they escalate. Organizations take a mean of 258 days to establish a breach. It is a time the place attackers can steal information, set up backdoors, and unfold throughout your infrastructure.
With out monitoring, you might solely uncover a problem after Google flags malware or shoppers report redirect injections. By that time, the injury to consumer belief and search rankings could already be important. Actual-time file integrity monitoring offers you the earliest potential warning.
How Efficiency and Cyber Safety Assist Advertising Businesses
Safety and efficiency aren’t separate priorities, they’re deeply linked. A safe atmosphere is nearly at all times a sooner, extra secure atmosphere.
Isolation Prevents Cross-Contamination
Fashionable infrastructure separates accounts to stop one compromised website from infecting others. Businesses profit considerably from containerized environments the place every consumer’s information stays contained. With out isolation, a single weak plugin on one consumer website might present attackers entry to your whole portfolio. Correct account segmentation turns what could possibly be a portfolio-wide disaster right into a manageable single-site incident. VPS internet hosting and devoted servers present the isolation companies want to guard a number of shoppers concurrently.
Fashionable Software program Improves Each Velocity and Safety
Working legacy PHP slows every thing: velocity, safety, and compatibility. Attackers goal outdated variations due to identified vulnerabilities. Your server software program should stay present, identical to your plugins. Fashionable PHP variations embrace efficiency optimizations that may enhance website velocity by 30% or extra whereas concurrently closing safety holes. This twin profit makes PHP updates one of many highest-value upkeep duties you possibly can carry out.
Correct Useful resource Dealing with Protects Excessive-Site visitors Websites
Marketing campaign site visitors spikes from paid advertisements, e mail campaigns, or product launches can expose weak methods. Misconfigured caching layers, file permissions, or useful resource allocations trigger efficiency drops and attackers steadily goal harassed websites. A website struggling below reputable site visitors turns into extra weak to useful resource exhaustion assaults. DDoS safety helps defend towards useful resource exhaustion assaults.
When your internet hosting makes use of NVMe storage, optimized PHP handlers, and scalable processing energy, you cut back the alternatives attackers have to use slowdowns. Managed WordPress internet hosting with correct useful resource dealing with means your websites stay responsive throughout site visitors surges, which protects each person expertise and safety posture.
Velocity Reduces Assault Home windows
Sluggish websites improve publicity to brute-force assaults, useful resource exhaustion, and bot probing. Quick web sites constructed for efficiency advertising and marketing, web optimization, or conversion ought to see safety and efficiency as the identical operational dedication. Response time issues for safety simply as a lot because it issues for conversion charges. When your infrastructure responds shortly to reputable requests, it could possibly additionally reply shortly to threats. This identifies and blocks malicious site visitors earlier than it causes injury.
Human Assist Issues Throughout Safety Occasions
Whenever you deal with dozens of consumer websites, assist high quality turns into a crucial safety issue. A difficulty affecting a single marketing campaign microsite on a Saturday evening can shortly flip into misplaced leads, wasted advert spend, and damaged reporting throughout a number of accounts.
Know Who You Can Attain in an Emergency
Many internet hosting suppliers depend on automated replies or outsourced assist. Throughout a malware occasion or account compromise, you want actual steerage from an skilled who can confirm logs, evaluate file constructions, and assist hint the foundation trigger. Generic troubleshooting steps waste crucial time throughout lively safety incidents. Direct entry to educated technicians who perceive your particular atmosphere can imply the distinction between a two-hour incident and a two-day disaster.
Perceive the Response Course of
Confirm your internet hosting supplier’s safety incident course of:
- Is malware cleanup steerage hands-on or generic?
- How shortly does assist help throughout lively incidents?
- Can technicians assist with file integrity checks or restoration?
- How do escalations work throughout a number of accounts?
Shield Shopper Belief
When a consumer’s marketing campaign microsite goes down or delicate information seems compromised, they count on speedy communication. Human assist supplies readability when automated scanners and generic articles can not. Purchasers don’t distinguish between internet hosting points and company points, they simply know their website is down. Your means to offer speedy, correct updates immediately impacts consumer retention. For shoppers in delicate industries like healthcare, breaches common $9.77 million in prices.
Dependable safety assist turns into an extension of your company’s credibility. When you possibly can shortly escalate points and obtain skilled help, you preserve consumer confidence even throughout safety incidents.
Construct Scalable, Segmented Environments
Safety improves dramatically when websites and accounts are structured accurately. Many companies place a number of consumer websites in a single shared area for comfort, however this creates pointless threat. Company internet hosting options and reseller internet hosting platforms present the infrastructure companies must handle a number of shoppers securely.
Separate Staging and Manufacturing
By no means carry out dwell edits on manufacturing websites. Staging environments allow you to take a look at updates, plugins, or efficiency adjustments with out risking dwell performance or exposing vulnerabilities. A correct staging workflow catches issues earlier than shoppers or their clients see them. Even easy adjustments can have sudden penalties: breaking crucial varieties, disrupting cost flows, or introducing compatibility points. Testing in staging protects each safety and consumer relationships. Free web site migration companies may help companies transfer consumer websites to safer environments.
Use Remoted Containers for Completely different Purchasers
Containerization protects accounts from cross-contamination. If one consumer’s website is compromised, remoted accounts restrict the unfold to others. This architectural choice essentially adjustments your threat profile. With out container isolation, attackers who achieve entry to 1 website can doubtlessly transfer laterally throughout your whole infrastructure, compromising dozens of consumer websites in a single incident. WordPress VPS internet hosting and devoted WordPress servers present the isolation companies want.
Keep away from Inserting All Shopper Websites in One Account
Shared account constructions create these issues:
- Shared credential entry
- Shared file paths
- Shared vulnerabilities
- Larger threat of widespread an infection
Understanding the variations between shared, VPS, and devoted internet hosting helps companies select the correct infrastructure for consumer safety.
Group Accounts by Sensitivity
Some consumer websites deal with extra personally identifiable data (PII) or cost information than others. Separating these websites into devoted environments provides a safety layer with out slowing improvement work. This segmentation technique enables you to apply stricter controls to high-risk websites whereas sustaining effectivity for less complicated initiatives. Analysis exhibits that 35% of knowledge breaches contain shadow information (unmanaged or untracked information saved exterior formal oversight) and these breaches price 16% greater than common.
Correct segmentation advantages each efficiency and safety containment. You possibly can allocate assets appropriately, implement focused monitoring, and adjust to client-specific safety necessities extra simply.
For advertising and marketing companies, cyber safety additionally means defending the broader advertising and marketing stack: CRMs, e mail platforms, analytics information, and advert accounts linked to consumer websites. Compromised web sites can result in poisoned monitoring, inaccurate attribution, and abuse of selling pixels or tags, all of which undermine marketing campaign efficiency.
Backups Are Non-Negotiable
Backups are the best preventative measure you possibly can implement. Undertake a multi-layer backup technique.
Computerized Each day Backups
Each website wants automated each day backups saved off-server. You can not depend on guide backups when juggling a number of shoppers, automation enforces consistency. Guide backup processes inevitably fail throughout busy intervals or workers transitions. Automated backups take away human error from the equation and guarantee each website receives the identical safety no matter undertaking precedence.
On-Demand Backups Earlier than Modifications
Earlier than putting in a plugin, performing a migration, or rolling out adjustments, create a restore level. If one thing breaks, you possibly can revert immediately. This easy behavior eliminates the panic that comes from harmful adjustments. On-demand backups take minutes to create however can save hours of reconstruction work when issues happen.
Clear Retention Insurance policies
Your retention settings ought to align with every consumer’s enterprise wants:
- Excessive-traffic ecommerce: Longer retention
- Small brochure website: Shorter retention acceptable
- Marketing campaign microsites: Frequent backups throughout lively intervals
Fast Restore Capabilities
When a website is compromised, you should restore it shortly and confirm integrity earlier than bringing it again on-line. Velocity issues for each safety and consumer confidence. A restore course of that takes hours as a substitute of minutes extends downtime and will increase consumer frustration. Your internet hosting atmosphere ought to assist one-click restores that carry websites again on-line in minutes, not hours.
Keep Redundant Copies for Crucial Websites
For crucial builds, hold a redundant copy exterior the internet hosting atmosphere. This protects you from uncommon however potential catastrophic failures. Off-site backups present insurance coverage towards eventualities like information middle failures, account-level compromises, or internet hosting supplier points.
Backups shield you from code errors, defective plugins, and cyberattacks. In addition they restore consumer belief immediately. When you possibly can recuperate from any incident shortly, shoppers see you as dependable and ready.
Malware Safety Should Be Steady
Even essentially the most safe atmosphere may be compromised via weak plugins, contaminated native machines, or compromised person accounts. Safeguarding your web site from malware requires steady monitoring and a number of layers of protection. Many hacks come from outdated software program or weak native units, not the server itself.
Automated Malware Scanning
Each day or steady scans detect malicious code, altered recordsdata, or injected scripts early. Early detection reduces cleanup time and limits injury. Automated scanning supplies constant monitoring that human evaluate can not match at scale. When managing dozens of consumer websites, automated malware detection turns into important for sustaining safety throughout your whole portfolio. Organizations utilizing intensive safety automation report breach prices averaging $2.2 million lower than these with out automation.
Alerts for Sudden File Modifications
Monitor core recordsdata, themes, plugins, and uploads. Even small adjustments can point out malware injection. File integrity monitoring supplies early warning of compromises that may in any other case go unnoticed for weeks. Attackers usually make delicate adjustments that don’t instantly break performance, permitting them to function undetected whereas stealing information or injecting spam hyperlinks. Safety analysis exhibits that thousands and thousands of cross-site scripting, SQL injection, and path traversal assaults goal WordPress websites each day.
Entry to Cleanup Instruments and Assist
You want direct entry to cleanup instruments or technicians who perceive methods to isolate malicious code, take away backdoors, and restore protected variations. Generic malware removing guides not often tackle the precise circumstances of your an infection. Skilled assist can differentiate between reputable recordsdata and cleverly disguised malware, lowering the danger of incomplete cleanups that go away backdoors lively.
Verification After Restoration
Restoring from backup removes injury, however verifying integrity prevents reinfection. Discover ways to recuperate from a web site hack with correct verification steps.
Your post-restoration guidelines ought to embrace:
- Checking all person accounts
- Updating plugins and themes
- Scanning native improvement machines
- Reviewing error logs
- Securing passwords and resetting MFA
Shopper Training and Documentation
Purchasers usually misunderstand malware and assume it signifies internet hosting failure. Assist them perceive how safety really works. Training transforms safety from a technical thriller right into a shared accountability. When shoppers perceive the connection between updates, plugins, and safety, they’re extra more likely to approve mandatory upkeep and fewer more likely to blame you for incidents past your management. WordPress safety greatest practices and preventative safety measures present frameworks for these conversations. Analysis exhibits that 827 deserted plugins have been reported in 2023 (almost six instances greater than in 2022) highlighting why lively upkeep issues.
Assist them perceive:
- How malware generally enters websites
- Why ongoing monitoring is critical
- Why outdated plugins are harmful
- What they’ll do to cut back threat
Deal with malware monitoring as a part of your consumer service providing, not merely a internet hosting characteristic. Place safety as an ongoing partnership that protects their enterprise pursuits.
SSL Is the Baseline, Not Elective
Search engines like google, browsers, and customers count on HTTPS in every single place. SSL is not a aggressive benefit, it’s the ground.
Each Website Wants an SSL Certificates
SSL is required for varieties, logins, ecommerce, and web optimization. Browsers more and more block non-HTTPS pages or show safety warnings that drive customers away instantly. These warnings create speedy belief issues that harm conversion charges and bounce charges. Google additionally makes use of HTTPS as a rating sign, that means websites with out SSL face each safety and web optimization disadvantages.
Certificates Should Renew Robotically
Guide renewals create threat. When managing dozens of domains, you want automated SSL with straightforward visibility into expiration dates. Guide monitoring methods fail throughout busy intervals or workers transitions. A single expired certificates can break crucial performance throughout a number of websites, creating cascading failures that have an effect on quite a few shoppers concurrently.
Expired SSL Breaks Crucial Performance
When SSL expires:
- Varieties cease sending
- Cost gateways fail
- Rankings drop
- Conversion funnels silently break
Confirm Redirects and Blended Content material
When migrating websites or adjusting domains, confirm all SSL-related configurations. Small misconfigurations can create silent failures that injury conversion charges with out triggering apparent errors. Blended content material warnings happen when HTTPS pages load HTTP assets, creating safety warnings that undermine person belief.
Confirm:
- 301 redirects
- Canonical settings
- Blended-content warnings
- CDN configurations
Don’t let SSL points create silent conversion losses. Common audits of SSL implementation shield each safety and income.
Set up Clear Deployment and Entry Insurance policies
Safety issues usually come from workflow errors moderately than infrastructure failures.
Use Model Management As a substitute of Stay Edits
Model management reduces unintentional overwrites and supplies accountability. Undertake Git-based workflows with clear branching methods. Model management creates a whole historical past of each change, making it straightforward to establish when and the way issues have been launched. This audit path turns into invaluable throughout safety investigations or when troubleshooting mysterious performance adjustments.
Retailer API Keys and Secrets and techniques Securely
By no means retailer credentials inside theme recordsdata, plugins, or publicly accessible folders. Use secret managers, atmosphere variables, or encrypted vaults. Hardcoded credentials in code repositories create safety vulnerabilities that persist for years. Even in the event you delete a file containing credentials, model management historical past could retain these secrets and techniques indefinitely, making them accessible to anybody who positive aspects repository entry.
Revoke Entry Instantly When Offboarding
Take away accounts, reset passwords, rotate API keys, and audit permissions the identical day a crew member or contractor departs. Delayed offboarding creates pointless safety home windows. Former crew members not often act maliciously, however their credentials may be compromised via phishing, information breaches, or gadget theft lengthy after they go away your group.
Apply Least-Privilege Rules
The default entry stage for any company person or consumer needs to be “minimal required to carry out their work.” Overly permissive entry creates pointless threat. Many safety incidents happen as a result of customers have entry to methods and information they don’t really need for his or her position.
A weak workflow introduces as a lot threat as a weak plugin. Securing code and infrastructure means nothing if workflow processes enable unauthorized adjustments or expose delicate information unnecessarily.
Shield Your Native Improvement Setting
Many infections originate on native units, particularly laptops that transfer between networks or belong to distant contractors.
How Shopper Websites Get Contaminated Regionally
An infection paths embrace:
- Developer machines operating outdated or unpatched software program
- Recordsdata moved between compromised laptops and staging environments
- Keyloggers or malware capturing panel credentials
- Session cookies stolen from insecure browsers
Mandate Safety Requirements for Improvement Machines
Your crew ought to comply with these practices:
- Common malware and antivirus scans
- Fast OS-level updates
- Present browser variations
- Safe WiFi use (keep away from public networks for deployments)
- Password managers for all credentials
- Encrypted onerous drives for machines dealing with consumer information
Safety doesn’t finish on the server, it extends to each gadget that touches consumer websites.
Educate Purchasers to Cut back Cyber Safety Threat
Purchasers are a part of your safety framework. An uninformed consumer can unintentionally undo your protections.
Assist Purchasers Perceive Key Safety Ideas
Cowl these subjects in consumer onboarding:
- Why updates matter: Skipping updates will increase threat, even when “every thing is working high-quality.”
- Why low cost or unverified plugins are harmful: Free plugins from unknown authors could embrace vulnerabilities or malicious code.
- Why safe varieties and cost workflows shield income: Safety lapses disrupt lead technology and ecommerce.
- Why admin entry needs to be restricted: Extra admin customers create extra alternatives for attackers.
- Why backups and monitoring are ongoing wants: Safety will not be a one-time setup; it’s steady upkeep.
Place Safety as Enterprise Safety
Body safety in phrases shoppers perceive: uptime, income safety, model fame, and buyer belief. When shoppers see safety as enterprise safety moderately than technical jargon, they’re extra more likely to assist mandatory investments. Join safety measures on to enterprise outcomes they care about: conversion charges, buyer information safety, and marketing campaign efficiency.
Shopper training reduces emergencies and strengthens your relationship. Nicely-informed shoppers change into companions in safety moderately than obstacles to mandatory upkeep.
Transferring Ahead
Safety for companies is about constructing methods that shield a number of shoppers concurrently whereas sustaining the pliability to ship inventive, high-performing web sites. The rules on this information type a basis that scales as your company grows.
Robust advertising and marketing company cyber safety isn’t simply threat administration, it’s a part of the way you shield marketing campaign efficiency, consumer belief, and long-term progress.
Begin by auditing your present safety posture towards these requirements. Establish gaps, prioritize enhancements, and doc your safety processes on your crew. When safety turns into a part of your operational tradition, it stops being a reactive burden and turns into a aggressive benefit.
Discover internet hosting options constructed for companies to seek out infrastructure that helps your safety requirements and enterprise progress.








