Final month, a mid-sized e-commerce firm misplaced all the pieces. Their internet hosting supplier, a price range choice with spectacular advertising,disappeared in a single day after a ransomware assault. No backup restoration. No help response. Only a clean web site and three years of buyer knowledge, gone.
Tales like this shouldn’t nonetheless occur in 2025, and but they do.
The internet hosting {industry} faces safety threats which can be evolving quicker than any single firm can deal with alone. DDoS assaults now attain 840 million packets per second, overwhelming even main infrastructure suppliers.
DDoS Assault
DDoS means Distributed Denial of Service. It’s an assault that tries to make a system or community unavailable by flooding it with visitors from a number of sources.
Ransomware gangs goal internet hosting firms particularly, realizing one breach can have an effect on hundreds of internet sites. And for each established internet hosting supplier working to take care of excessive requirements, there are dozens of fly-by-night operators racing to the underside on value, slicing corners on safety, and placing their clients in danger.
Right here’s the issue that retains me up at evening: how does a small enterprise proprietor know which internet hosting supplier they’ll truly belief?
Conventional alerts don’t work anymore. Advertising and marketing claims are simple to make, and testimonials will be manufactured.
Even value isn’t a dependable indicator —costly doesn’t assure high quality, and low-cost doesn’t all the time imply slicing corners. The internet hosting {industry} has by no means had a standardized method for patrons to confirm that their supplier follows primary safety and operational requirements.
Till now, each internet hosting firm has confronted these challenges alone. We’ve every constructed our personal safety protocols, developed our personal abuse response procedures, and tried to remain forward of threats independently.
However the web doesn’t work in isolation, and neither ought to the businesses that host it. That’s why DreamHost joined the Safe Internet hosting Alliance as a founding member —and why we spent the final yr working with {industry} friends to construct one thing larger than any single firm might create by itself.
Associated Submit: [STUDY] 12% of Small Companies Say They’ve Paid a Ransom Demand
The Verification Vacuum and Why Belief Issues Extra Than Ever
Too many internet hosting suppliers prioritize short-term income over long-term reliability. They provide rock-bottom costs, make guarantees they’ll’t maintain, and infrequently lack the infrastructure or experience to deal with safety threats. Some disappear solely when issues come up, leaving clients with no recourse.
These sorts of suppliers persist as a result of the internet hosting market has spent a long time competing totally on value. When clients can’t simply confirm high quality variations between suppliers, value turns into the deciding issue. This creates a race to the underside that rewards the most affordable choice, not probably the most safe or dependable one.
The results for companies are actual and devastating:
- Misplaced knowledge means misplaced income, misplaced buyer belief, and typically misplaced companies solely.
- Prolonged downtime throughout essential launches or gross sales intervals prices hundreds of {dollars} per hour.
- Safety breaches expose buyer info, creating authorized legal responsibility and reputational injury that takes years to get better from.
- Poor abuse response will get your web site caught in spam blacklists or malware warnings, destroying your search rankings in a single day.
However how do you, as a enterprise proprietor, know if a internet hosting supplier has real abuse mitigation procedures or simply advertising copy? How do you confirm they’ll reply to abuse studies, keep your uptime, and deal with authorities knowledge requests lawfully?
Earlier than the Safe Internet hosting Alliance’s certification program got here alongside, you couldn’t. There was no standardized certification, no industry-wide verification system, and no solution to independently affirm that you simply had been selecting a internet hosting supplier that adopted primary safety and operational requirements.
Different industries have solved this downside —you search for safety badges when procuring on-line, belief seals from cost processors, and certifications from monetary establishments. Healthcare suppliers show their accreditations.
However internet hosting? We’ve been working in a belief vacuum, asking clients to take our phrase for it.
That needed to change. The internet hosting {industry} wanted a solution to make trustworthiness seen and verifiable — not simply claimed, however demonstrated and independently licensed.
The Safe Internet hosting Alliance: A Collaborative Strategy
The Safe Internet hosting Alliance launched a few yr in the past as an initiative of the Web Infrastructure Coalition (i2Coalition). The i2Coalition shaped through the 2011 struggle towards SOPA and PIPA laws, and is the main voice for firms that construct the Web’s infrastructure.

The SHA represents progress within the coalition’s actions, targeted round reactive coverage protection, to now embrace proactive {industry} enchancment. Slightly than ready for issues to drive change, various internet hosting suppliers and affiliated firms got here collectively to determine requirements defining what accountable internet hosting truly means.
To this point, 26 on-line service suppliers have turn out to be Safe Internet hosting Alliance Licensed. Certificants embrace main gamers throughout the internet hosting spectrum. DreamHost, Automattic, Hostinger, BigScoots, and GoDaddy, simply to call a couple of.
4 Key SHA Objectives
The SHA exists to remodel how the internet hosting {industry} operates. We’re working towards 4 interconnected targets that deal with the {industry}’s most urgent challenges.
1. Develop a cooperative framework for fraud prevention and abuse response.
Safety threats don’t respect firm boundaries. When one internet hosting supplier will get exploited for phishing or malware distribution, it damages belief in all the {industry}.
The SHA creates channels for member firms to share menace intelligence, coordinate takedown responses, and work successfully with regulation enforcement. This collaboration makes all of us simpler at defending clients.
2. Set up frequent {industry} requirements for privateness, safety, and transparency.
For too lengthy, “safe internet hosting” has meant no matter every firm needed it to imply. The SHA’s certification program defines particular, measurable requirements round transparency, infrastructure misuse protocols, community reliability, and authorities request dealing with that clients can depend on. These are concrete operational necessities that licensed suppliers should exhibit and keep.
3. Create a unified language and taxonomy for the hosting {industry}.
When each firm makes use of totally different phrases to explain related providers or safety measures, clients can’t make significant comparisons. Standardized terminology makes it simpler for patrons to grasp what they’re shopping for.
It additionally helps the {industry} coordinate on shared challenges, as a result of clear definitions allow higher communication between suppliers, regulation enforcement, and regulators.
4. Contribute to legislative and regulatory discussions with knowledgeable {industry} views.
Lawmakers and regulators usually lack technical understanding of how internet hosting infrastructure truly works. After they attempt to clear up reliable issues, like on-line abuse or knowledge safety, with out {industry} enter, they danger creating rules that sound good however don’t work in apply. The SHA offers policymakers entry to collective {industry} experience.
These 4 targets work collectively to create an atmosphere the place accountable internet hosting suppliers can thrive — clients could make knowledgeable selections, and all the Web infrastructure turns into extra resilient.
The Belief Seal: Making Trustworthiness Seen
The SHA Belief Seal is the place all this work turns into tangible for patrons. It’s the seen image {that a} internet hosting supplier has been independently verified to satisfy rigorous operational, safety, and moral requirements.
Consider it just like the safety badges you see when testing on-line, or the certifications displayed in a physician’s workplace.
The internet hosting {industry} has by no means had this.
Incomes SHA certification isn’t computerized, even for founding members who helped create the requirements. Every internet hosting supplier should exhibit compliance throughout 4 interconnected pillars. The certification course of includes documentation overview, coverage verification, and ongoing accountability to take care of the seal.
The 4 Pillars of SHA Certification
SHA certification evaluates internet hosting suppliers throughout 4 essential operational areas:
| Pillar | What It Requires | Why It’s Essential |
| Transparency | Clear, publicly accessible insurance policies together with Acceptable Use Coverage, phrases of service, and documented operational procedures. | Prospects know precisely what guidelines apply, what to anticipate, and the way the supplier operates. |
| Infrastructure Misuse Protocols | Documented contacts and response procedures with prioritized dealing with of confirmed abuse studies and safety threats. | When safety points come up, they get addressed shortly and professionally slightly than ignored or delayed. |
| Community Useful resource Reliability | Proactive monitoring, complete restoration planning, and capability administration to make sure constant uptime. | Your web site stays on-line once you want it, backed by documented catastrophe restoration and redundancy. |
| Authorities Request Dealing with | Lawful, well-documented procedures for dealing with knowledge requests that shield person rights whereas assembly authorized obligations. | Your knowledge will get the due course of safety it deserves, with clear insurance policies on when and the way info is disclosed. |
Why DreamHost Joined the SHA
After we first heard concerning the Safe Internet hosting Alliance and its targets, my speedy response was easy: “None of that is new for us.” They had been advocating for hosts to undertake insurance policies that replicate how DreamHost has executed enterprise for the final 25 years. Signing on was a no brainer. However that’s solely a part of the story.
We joined the SHA as a founding member for 3 causes:
1. Safety threats require collaborative options, not particular person heroics
When malware spreads by means of compromised internet hosting accounts or phishing campaigns exploit lax safety at one supplier, it damages buyer belief throughout all internet hosting providers.
We will construct probably the most sturdy safety infrastructure on this planet at DreamHost, but when clients can’t inform us aside from a much less reliable operation, we’re all competing in a race to the underside.
The SHA working group meets month-to-month to debate safety traits. When one member identifies a brand new assault vector or discovers a very refined fraud operation, everybody advantages from that data.
2. Unbiased possession offers us the liberty to prioritize {industry} well being
DreamHost has all the time been independently owned. We don’t reply to traders demanding we maximize quarterly earnings. That independence means we are able to take part in initiatives just like the SHA as a result of they’re the precise factor for the {industry} and our clients.
Many internet hosting suppliers function as subsidiaries of bigger expertise conglomerates or non-public fairness portfolios. These possession constructions create stress to concentrate on particular person firm efficiency slightly than industry-wide enhancements. We don’t face these constraints.
3. Constitution member standing gave us a voice in defining “safe internet hosting”
Requirements created with out enter from firms that really function internet hosting infrastructure are usually both too imprecise to imply something or too inflexible to work in apply. We spent months in working group periods with engineers, safety professionals, and operations leaders from different founding members.
We hammered out necessities that might be each rigorous and achievable.
What particular response time ought to abuse studies require? How do you doc authorities request dealing with procedures in ways in which shield buyer privateness whereas remaining legally compliant? What does “proactive monitoring” imply in concrete phrases?
The SHA transforms “belief us” into “confirm us.”
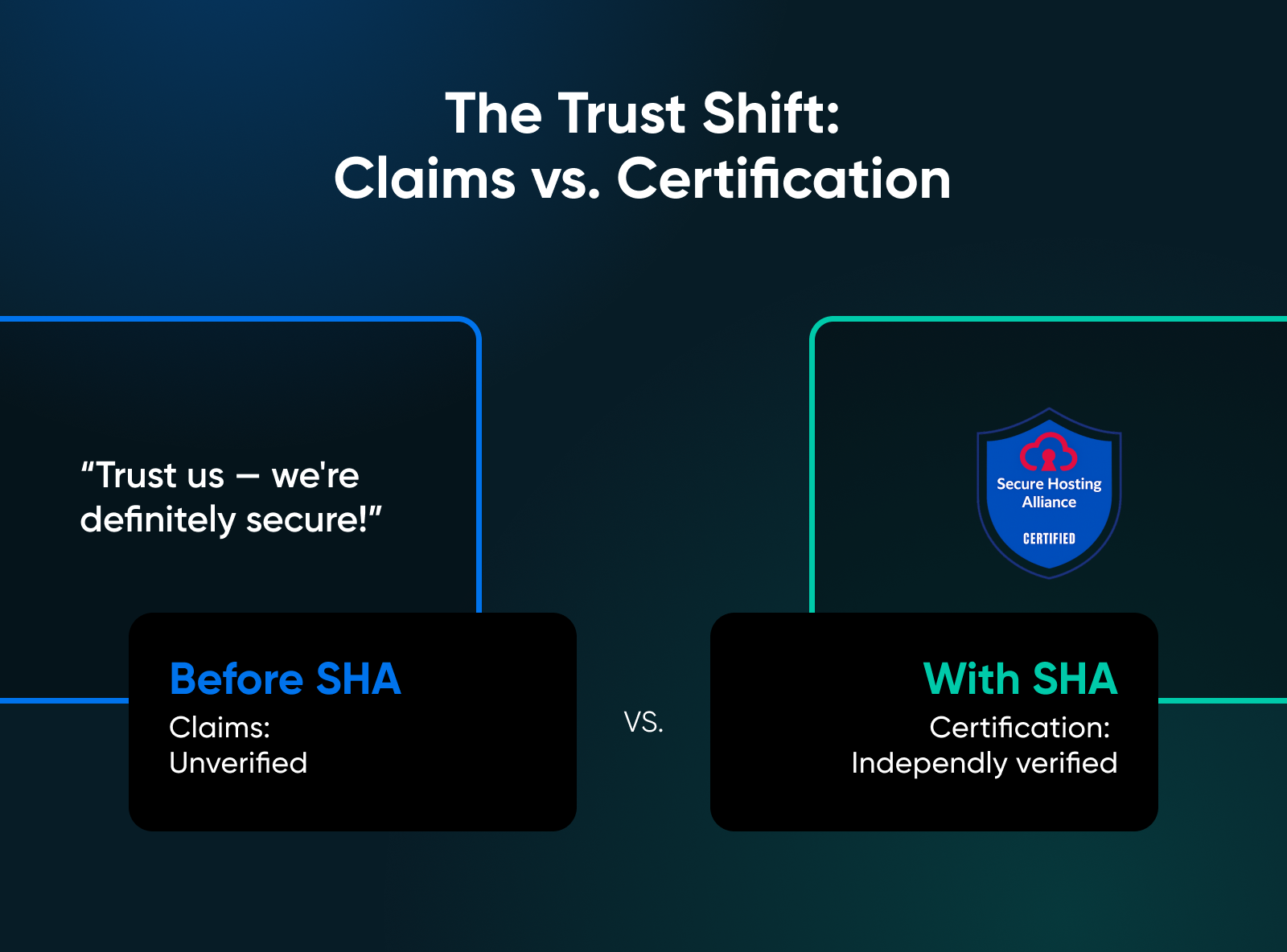
As a substitute of evaluating advertising guarantees, clients can evaluate certifications. As a substitute of hoping a supplier follows good safety practices for WordPress internet hosting, they’ll confirm it by means of a SHA certification.
DreamHost is SHA licensed, validating practices we’ve maintained all through our historical past. However the certification itself isn’t the achievement we’re most pleased with. It’s the collaborative framework we helped construct that can increase requirements throughout all the {industry}. That’s the true worth of the Safe Internet hosting Alliance.
Associated Submit: DreamHost Achieves Safe Internet hosting Alliance Certification
Trying Forward to the Way forward for Safe Internet hosting
The SHA Belief Seal isn’t a end line, however a place to begin for steady enchancment in how the internet hosting {industry} protects clients and maintains belief.
We proceed attending month-to-month SHA working group conferences that give us perception into assaults focusing on different suppliers earlier than they attain our infrastructure. They assist us reply quicker when threats do emerge. This month-to-month coordination with {industry} friends represents a basic shift in how internet hosting safety works.
Internet hosting safety has all the time required collaborative options. Particular person firms, irrespective of how giant or well-resourced, can’t clear up ecosystem-wide challenges alone.
Whenever you see the SHA Belief Seal on a internet hosting supplier’s web site, you’re seeing proof of ongoing accountability. You’re seeing clear insurance policies, responsive abuse dealing with, dependable infrastructure, and lawful knowledge safety.
The SHA gives requirements, certification, and ongoing accountability. The remainder is as much as us — internet hosting suppliers keen to satisfy these requirements, and clients keen to prioritize verified trustworthiness over the bottom value.
Study extra concerning the Safe Internet hosting Alliance and its certification program at hostingsecurity.internet.
Did you take pleasure in this text?









