TL;DR: In 2025, the scariest web site safety dangers haven’t come from WordPress core — they’ve come from weak plugins, uncared for themes, and unpatched server software program like OpenSSH and PHP on Ubuntu.
These are the 10 most impactful vulnerabilities to date this yr, together with how they labored and what classes website homeowners and builders ought to take away. The underside line: constant updates, cautious position administration, and a focus to safety advisories are what maintain your internet hosting tales from turning into horror tales.
It at all times begins the identical approach.
A late-night ping. A panicked shopper. A WordPress website that was working tremendous yesterday, however is now coughing up error logs and redirecting guests to a sketchy pharmacy area. In your thoughts, all you’ll be able to hear is the screeching violins from a horror soundtrack.
Most scary internet hosting tales aren’t brought on by the ghosts and monsters of spooky season fame. They arrive from vulnerabilities left unpatched just a bit too lengthy. In 2025, the actual hazard hasn’t been WordPress core (which has solely had one notable subject this yr up to now), however fairly the plugins, themes, and server software program that energy your website.
That’s why we’re right here, flashlight in hand, to stroll you thru the highest 10 vulnerabilities that despatched shivers down builders’ spines this yr. These aren’t cautionary tales meant to scare you away from the online. They’re area notes from the entrance strains —classes you should utilize to maintain your internet hosting tales from turning into horror tales. Let’s dive in.
What Does the 2025 Risk Panorama Look Like for WordPress Plugins and Ubuntu Packages?
Plugins and themes are the place virtually all of the WordPress danger lives. In 2025, WordPress core has seen just one main vulnerability to date, however the plugin and theme ecosystem has already produced shut to eight,000 vulnerabilities as of September (after we wrote this text).
Mid-year studies verify not solely the excessive quantity, however excessive real-world exploitability. 6,700 vulnerabilities had been recognized within the first half of the yr, with 41% categorised as exploitable in real-life assaults.
Ubuntu’s safety notices (USNs) present common, clear updates for points throughout supported releases. A lot of these USNs cowl crucial software program generally utilized in internet hosting environments (PHP, OpenSSH, libraries like libxml2, and so on.). Between January and August 2025, Canonical revealed 829 USNs protecting 7,408 distinctive CVEs throughout the supported releases. That already outpaces all of 2024, which noticed 884 USNs addressing 5,611 CVEs.
The sample is obvious: the quantity of OS-level vulnerabilities is accelerating, usually overlapping in danger with plugin and theme leaks.
So what can enterprise homeowners take away from the menace panorama in 2025? There’s three main issues:
- You’ll be able to’t depend on core for defense – The true hazard comes from third-party code in plugins and themes, as a result of that’s the place the vulnerabilities are multiplying.
- Exploitability is rising – And it’s not simply extra bugs. A rising share of these bugs can be utilized in assaults proper now.
- OS vulnerabilities compound danger – Even when WordPress code is sound, the outdated or weak Ubuntu packages can widen the assault floor dramatically.
The ten Scary Tales of 2025: What Went Incorrect (and What Can We Be taught From It)?
Under are the actual vulnerabilities that shook the WordPress plugin ecosystem this yr (to date). Understand that these aren’t historical historical past —many websites are nonetheless uncovered except patched.
1. Submit SMTP
What occurred: Model ≤ 3.2.0 of the Submit SMTP WordPress plugin had a damaged entry management in one among its REST API endpoints (the get_logs_permission perform). The perform solely checked if a consumer was logged in, not whether or not they had ample privileges (for instance, Administrator).
Due to this, even Subscriber-level customers might fetch electronic mail logs, view electronic mail our bodies, and intercept password reset emails meant for higher-privilege customers. Yikes!
E mail logs usually embrace delicate particulars. Intercepting password resets means a low-privilege consumer might reset an admin’s password and take over the positioning. That turns what looks as if a innocent plugin bug into full-site compromise.
Plus, Submit SMTP is broadly used, with over 400,000 energetic installations. A big slice of these websites had been working weak variations on the time of disclosure.
Key takeaway: Even easy checks (is_user_logged_in) aren’t sufficient for delicate knowledge. Privilege checks should match the sensitivity of the endpoint.
2. Important Addons for Elementor
What occurred: Variations ≤ 6.0.14 of Important Addons for Elementor had a mirrored Cross-Web site Scripting (XSS) vulnerability within the popup-selector question argument. Enter was not correctly sanitized/validated earlier than being embedded into web page output. The flaw was mounted in model 6.0.15.
This plugin has over 2 million installations, so a vulnerability like this has a big potential attain. Mirrored XSS can allow phishing, credential theft, token hijacking, or defacement if an attacker methods a consumer into clicking a crafted URL. The size of energetic installs means many websites had been uncovered.
Key takeaway: Common plugin + easy enter vector = widespread danger. A big set up base magnifies even “simply XSS” vulnerabilities.
3. WPForms Lite
What occurred: WPForms Lite variations as much as 1.9.5 had been weak to saved Cross-Web site Scripting through the start_timestamp parameter. Authenticated customers with Contributor position or above might inject scripts that persist and run each time a consumer views a compromised web page.
As a result of contributor-level entry is usually granted (or unintentionally stored) on websites with a number of authors or workforce members, the chance was actual. The power to persist script injection means compromise can stay till the positioning code or database is cleaned —not only a one-time mirrored assault.
Whereas the CVSS severity is “medium” (5.4) for this subject, persistent XSS is more durable to detect, more durable to wash, and carries larger penalties (cookie theft, privilege escalation, consumer belief loss) than many individuals notice.
Key takeaway: Saved XSS through decrease position customers is harmful. Permissions matter, as does guaranteeing even “trusted” customers aren’t robotically protected.
4. GiveWP
What occurred: Variations of GiveWP earlier than 3.19.4 contained a PHP Object Injection vulnerability. Enter handed to sure unserialize features wasn’t validated, permitting crafted payloads to be injected. Underneath some PHP configurations, this might allow attackers to set off “magic strategies” in courses, resulting in Distant Code Execution (RCE).
GiveWP is without doubt one of the hottest donation plugins, powering over 100,000 energetic installations. Websites that depend on it for nonprofit fundraising might have had their servers hijacked, not simply their front-end shows. That’s each a enterprise continuity and belief catastrophe.
Key takeaway: Complicated plugins like donation platforms deal with delicate knowledge, which makes them prime targets. At all times patch them shortly.
5. AI Engine Plugin
What occurred: The AI Engine plugin by Meow Apps shipped a model that lacked entry checks, permitting customers with minimal roles to escalate their privileges. This meant an attacker who might register as a primary consumer might promote themselves to Administrator.
Privilege escalation vulnerabilities are among the many most devastating as a result of they subvert the belief mannequin. A registered consumer (or in some circumstances even a bot creating a brand new account) might immediately achieve management of the whole website. With AI Engine broadly adopted to combine OpenAI and different AI providers, the blast radius prolonged to each advertising and marketing and manufacturing web sites.
Key takeaway: Privilege escalation is scarier than XSS as a result of it fingers attackers the keys to your website. Position audits ought to be a part of each month-to-month upkeep routine.
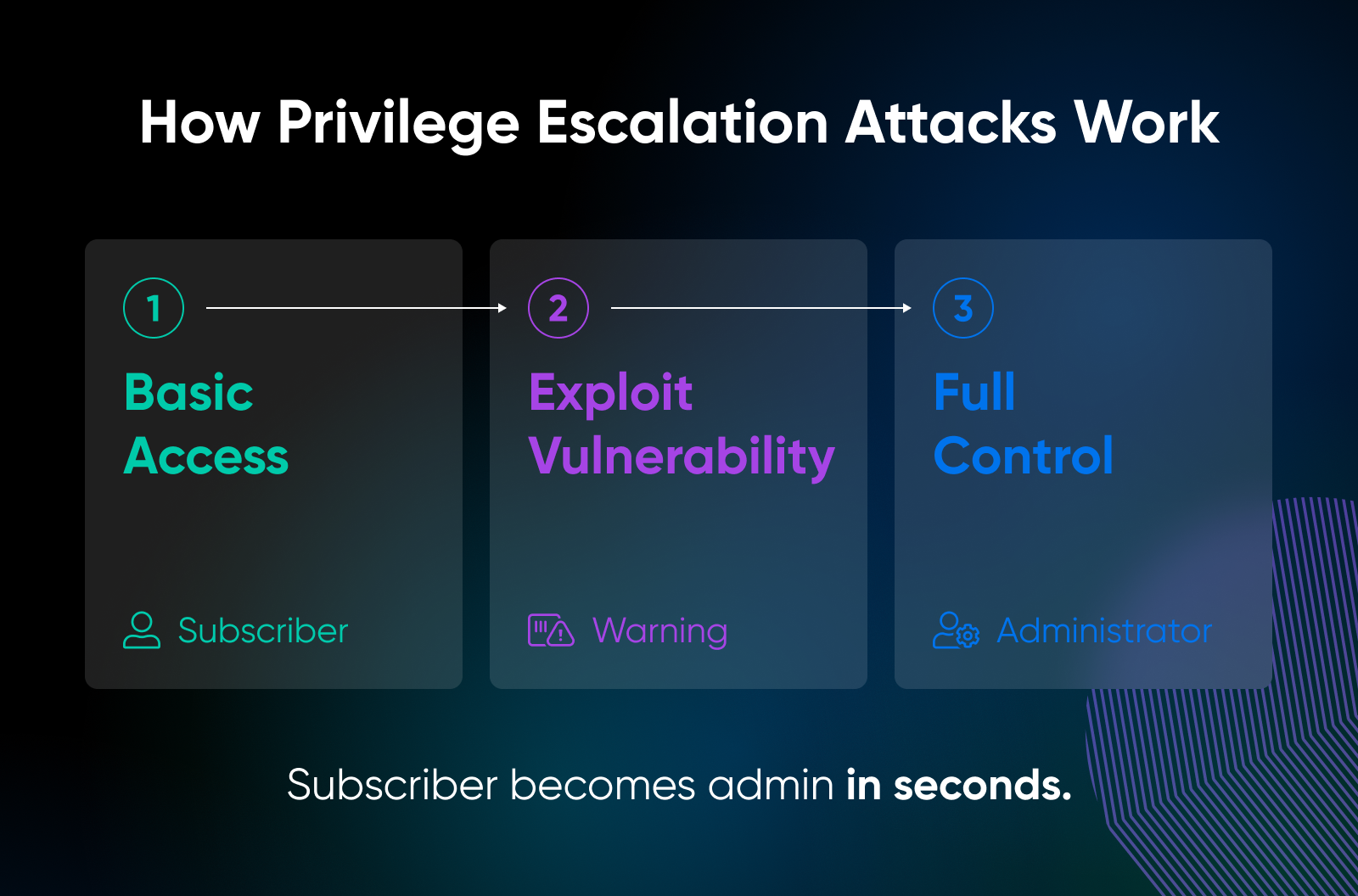
6. B Blocks Plugin
What occurred: B Blocks, a WordPress plugin with tens of 1000’s of installs, had a crucial flaw: lacking authorization checks allowed unauthenticated guests to create new administrator accounts. In contrast to different privilege escalation bugs, this one didn’t require any consumer position or login in any respect.
Any attacker who knew the endpoint might spin up a model new admin account. From there, they might set up backdoors, export the database, or inject website positioning spam hyperlinks throughout the positioning. As a result of it didn’t require current entry, this bug was closely exploited within the wild shortly after disclosure.
Key takeaway: Unauthenticated privilege escalation is as dangerous because it will get. Each website proprietor ought to commonly examine their consumer listing, even once they suppose every thing is patched.
7. Motors Theme
What occurred: The Motors theme, broadly used for automotive dealership and auto market websites, contained a privilege escalation flaw. The vulnerability allowed unauthenticated attackers to use weak checks within the theme code to realize administrator-level privileges.
In contrast to small area of interest themes, Motors is industrial and closely adopted. A compromised theme at this scale means 1000’s of enterprise websites promoting stock, funds, and buyer leads are immediately uncovered. Privilege escalation right here means attackers didn’t should be intelligent — they might merely “stroll in” and promote themselves.
Key takeaway: Themes might be as harmful as plugins. In the event you purchased a theme years in the past and haven’t up to date it, that theme could also be your weakest hyperlink.
8. Database for Contact Kind 7 / WPForms / Elementor Kinds
What occurred: The Database for CF7, WPForms, and Elementor Kinds plugin had a crucial Distant Code Execution / Denial of Service vulnerability. Variations ≤ 1.4.3 didn’t sanitize user-supplied inputs, letting attackers inject malicious payloads by means of type submissions.
As a result of this plugin is an add-on to a few of the preferred type builders, the publicity was amplified. An attacker might submit a “innocent” type however truly plant code in your server — a nightmare state of affairs for companies managing a number of shopper websites.
Key takeaway: Even small “helper” plugins can convey down a complete stack. In the event you lengthen crucial plugins with add-ons, patch them simply as urgently as the principle instrument.

9. OpenSSH on Ubuntu 24.04
What occurred: Canonical disclosed a number of OpenSSH vulnerabilities in 2025, together with a forwarding bypass flaw the place the DisableForwarding directive didn’t work as meant (USN-7457-1). One other advisory (USN-7270-1) addressed potential denial-of-service dangers in shopper connections.
OpenSSH is without doubt one of the most foundational packages on Ubuntu servers. If SSH entry is uncovered, attackers can chain these bugs to realize persistence or disrupt availability. Many sysadmins assume SSH is protected by default, however vulnerabilities like these present that even the hardened core wants vigilance.
Key takeaway: Don’t assume crucial packages are invulnerable. Even mature software program like OpenSSH wants fixed patching and config evaluate.
10. PHP on Ubuntu
What occurred: A vulnerability in PHP’s SOAP/XML parsing allowed crafted payloads with malformed namespace prefixes to set off crashes. Canonical rolled this into USN-7648-1, which patched the difficulty on supported Ubuntu variations.
Many WordPress plugins and themes rely upon PHP SOAP/XML features for integrations (fee gateways, CRMs, advertising and marketing automation). A crash on the PHP interpreter layer means full denial of service, and each website on that server could possibly be affected.
Key takeaway: Server software program flaws are simply as threatening as WordPress bugs. In case your PHP course of dies, your website dies with it.
What These Tales Train Us
Taken collectively, these 10 circumstances inform a constant story: The scariest vulnerabilities in 2025 haven’t been unique zero-days in WordPress core. They’ve been the on a regular basis cracks within the partitions: outdated plugins, uncared for themes, and unpatched server software program.
Three classes stand out:
- Plugins and themes are the weakest hyperlink. Common add-ons drive most WordPress vulnerabilities, and their giant set up bases make them prime targets.
- Privilege escalation is in all places. From Submit SMTP to the AI Engine plugin, attackers are on the lookout for shortcuts to admin rights. As soon as they’ve these, every thing else is secondary.
- OS-level bugs matter as a lot as utility bugs. OpenSSH and PHP flaws remind us that protecting Ubuntu packages present is simply as necessary as updating WordPress itself.

The takeaway isn’t to worry your software program stack, however to respect it and maintain it. Each plugin, theme, or server bundle you put in widens the floor space for assault. The distinction between a scary internet hosting story and a routine patch cycle is how shortly you notice and tackle these dangers.
Safety doesn’t should be terrifying. With constant updates, cautious position administration, and a focus to advisories, you’ll be able to maintain the monsters at bay.

Unbeatable WordPress Internet hosting
Dependable, lightning-fast internet hosting options particularly optimized for WordPress.
Did you take pleasure in this text?









