Knowledge breaches aren’t uncommon anymore — they’re merely a part of the background hum that underlies our digital world.
Chances are high, you’ve already been caught within the sophisticated internet of 1.
Possibly you even acquired an electronic mail from an organization saying your information was uncovered. And even in case you didn’t, that doesn’t imply you have been spared. It simply implies that nobody advised you.
Even in case you’re tremendous cautious on-line, your info can nonetheless find yourself within the flawed fingers, however you’re not helpless.
You’ll be able to shield your self proper now.
Perceive how information breaches have an effect on individuals at the moment, study what private particulars it is best to concentrate on defending, and comply with our steps to safe your information from being compromised.
It’s all under.
The Influence of Knowledge Breaches As we speak
An information breach happens when somebody malicious (normally known as a “unhealthy actor”) beneficial properties unauthorized entry to delicate info they shouldn’t have entry to. They do that through hacking or discovering a “backdoor” right into a less-than-secure information storage system.
Knowledge breaches can result in id theft, fraudulent account creation in your identify, account takeovers, and ransom threats. Hackers could steal monetary information or use your private particulars to conduct phishing scams, the place they craft emails that look convincingly actual to trick you or somebody you already know into giving up cash or delicate particulars.
The fallout from a knowledge breach can embody misplaced cash, harm to your credit score rating, hurt to your fame, and the daunting activity of rebuilding your digital accounts from scratch.
As extra of our private information is saved on-line and AI-powered know-how makes it simpler to create nefarious data-farming applications, these breaches have gotten extra highly effective and prevalent!
An information breach isn’t simply an summary idea that occurs to huge companies and people with tons of belongings to loot.
Even in case you aren’t conscious of it, you’ve doubtless been impacted by somebody meddling together with your private info.
Take, for instance, the 2024 cyberattack on the huge well being fee processing firm Change Healthcare, known as “probably the most important and consequential incident of its type in opposition to the [U.S.] well being care system in historical past” by Rick Pollack, President and CEO of the American Hospital Affiliation.
The hacker group stole this information to gather ransom on it, which delayed medical take care of tens of millions of individuals and put many smaller medical practices in peril of closing on account of misplaced income.
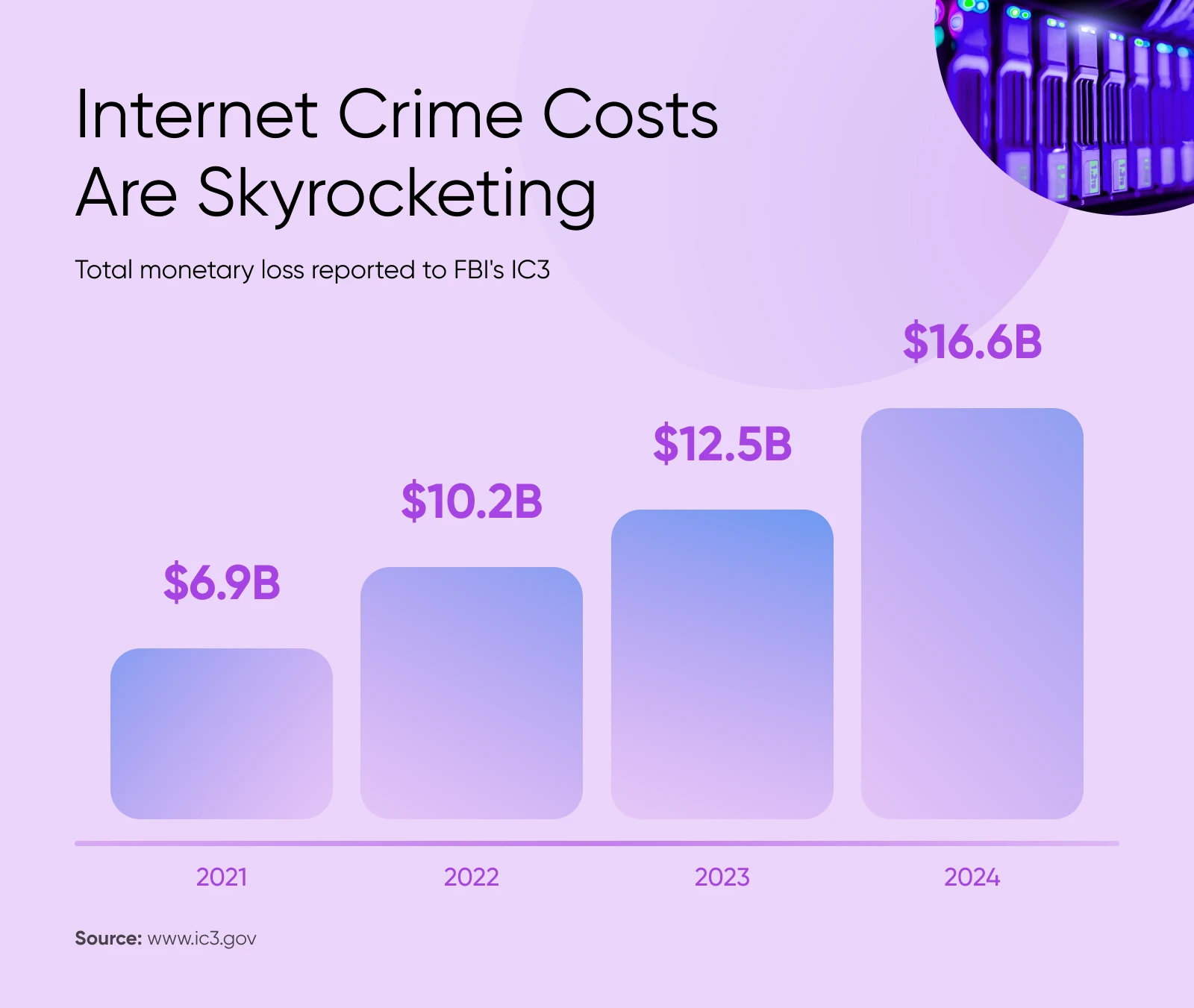
In keeping with the FBI’s Web Crime Grievance Heart (IC3), the place tons of of 1000’s of people doc cyber crimes yearly, information breaches have been one of many prime complaints in 2024. And whole financial loss on account of web crimes continues to develop by leaps and bounds.
What Private Knowledge Do I Want To Shield?
Each time you employ an app, go to a web site, and even submit on social media, you’re doubtless sharing small items of private info that must be protected.
This may embody issues like…
- Your full identify
- Your passwords
- Your social safety quantity
- Your birthday
- Your location
- Your medical information
- Your relationships
- Your web historical past
- Your system particulars
- Your shopping habits
How does this occur?
Usually, you share info like this once you create an internet account or make a fee. As well as, many corporations acquire this information utilizing cookies and trackers to supply customized promoting and experiences in return.
16 Methods To Safeguard Your Private Knowledge on the Web
Regardless of whether or not you’ve shared info deliberately or it’s gathered quietly within the background by the instruments you employ, listed here are 16 suggestions it is best to implement proper now to guard your private information to the perfect of your capability.
Restrict What You Share
A straightforward place to start out is tobe aware of the knowledge you place on-line. Solely share essential private info.
The much less information you make publicly out there, the more durable it’s for hackers and information brokers to use you.
Develop Totally different Identities for On-line Use
Take into account sharing completely different quantities or varieties of info relying on what you’re doing on-line.
Whereas your financial institution does have to know quite a lot of details about you, does a social media web site actually need your full identify, electronic mail tackle, and birthday?
Developing with a number of personas with various levels of element and accuracy can assist you restrict how a lot delicate info you share and higher management which internet sites get a portrayal of your full id.
Consider Each New Account
Generally, you may nearly see a knowledge breach coming when you think about an organization’s practices, origins, and enterprise mannequin.
Not all apps and platforms will deal with information responsibly. Decide how a lot you belief a brand new service you’re signing up for with the following pointers:
- Search for person critiques within the app retailer, on Reddit, and on YouTube.
- Try the privateness coverage. It ought to be straightforward to search out, simple, and embody contact info for the corporate.
- Take into account how the platform makes cash. If it’s free, what are they promoting (your contact info, your behavioral information, and so forth.) to show a revenue?
- Take into account the world of origin. Companies outdoors your state or nation might have lax safety rules.
- Does the URL within the tackle bar comprise “https” and a lock icon? This ensures its TLS certificates is updated, making it extra more likely to be safe and above board.
- Discover a sudden uptick in spam? That may very well be linked to info you’ve lately shared with a brand new platform.
Know Thy Enemy
Keep updated on what sorts of organizations and persons are on the market gathering information, how they’re at present utilizing it to conduct scams, and what finest practices safety professionals advocate.
Use a VPN When in Public
Public Wi-Fi is notoriously susceptible to hackers. A VPN is a service you may subscribe to that encrypts your web connection, protecting your information protected even when your connection is lower than non-public.
Be sure you apply it to all gadgets when accessing public networks!
Don’t Ignore These Replace Reminders
Certain, it’s straightforward to simply click on away these little safety replace pop-ups that all the time appear to come up once you’re proper in the midst of one thing. Keep away from the temptation!
Set up updates on your working methods, apps, and gadgets promptly to guard in opposition to the newest threats. These updates aren’t all the time nearly implementing cool new performance; they typically additionally embody essential safety patches.
In case your system has a setting to automate the replace course of, we advocate turning that on so that you don’t even have the possibility to overlook.
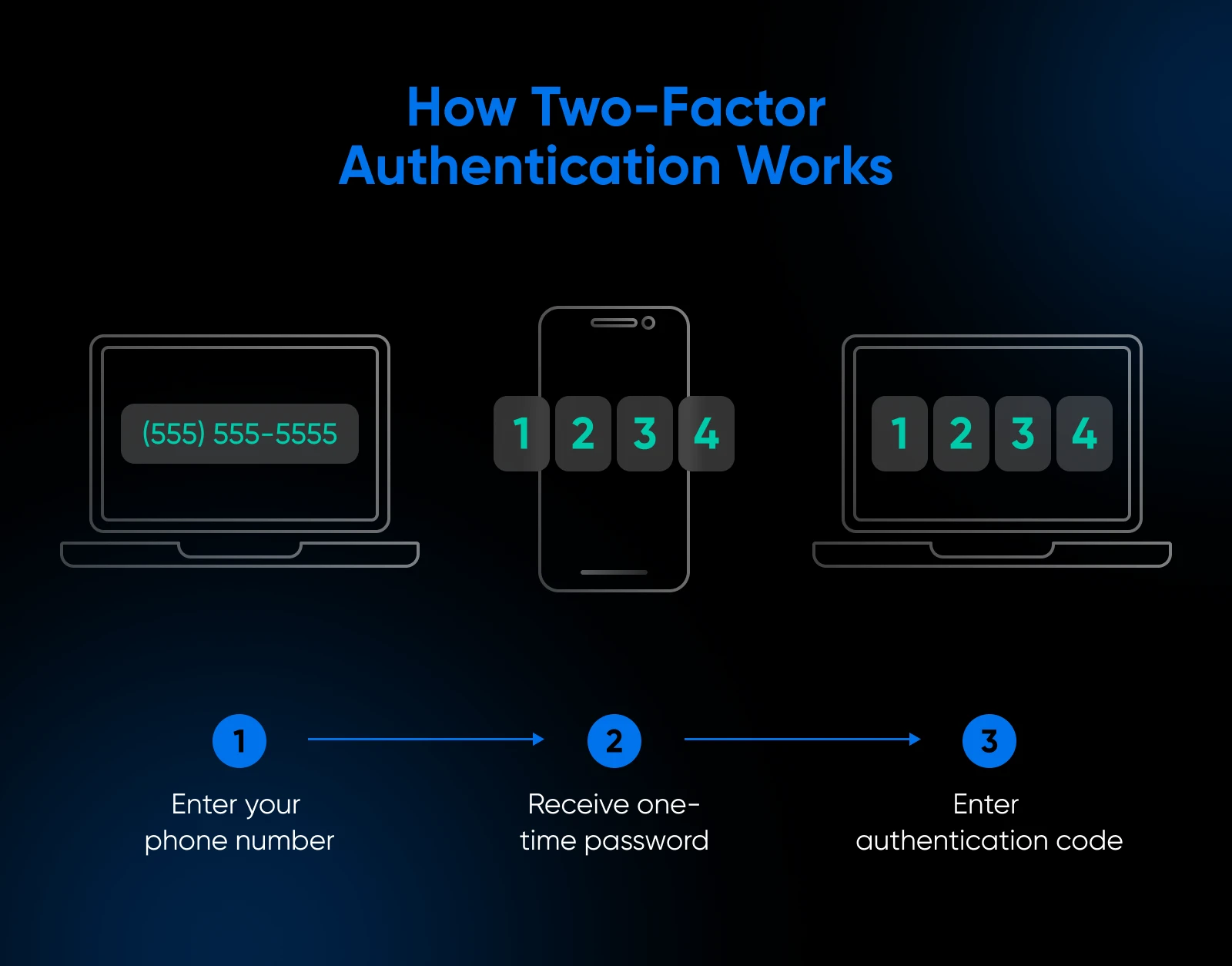
Set Up 2FA
Two-factor authentication (2FA) provides an additional layer of safety by requiring a code or verification that’s despatched to a different account or system — all along with your password.
Even when somebody steals your password, they will’t entry your account with out the second issue. Except for sturdy passwords, 2FA is likely one of the easiest and finest methods to indicate hackers you’re no straightforward goal.
Restrict Huge Tech’s Entry to Your Life
It’s most likely no shock that Amazon collects a enormous quantity of information about your purchasing habits. The one method to absolutely escape its monitoring is to cease purchasing there completely, however you may nonetheless take steps to cut back how your information is used.
For instance, you may forestall Amazon from utilizing your information for customized adverts. And in case you use the Alexa service or any Amazon-owned gadgets (equivalent to Kindle), you may change what sort of info these acquire.
This text makes the method straightforward.
Click on Discriminately
Keep away from clicking on pop-ups, texts, hyperlinks, and attachments —or something that you simply don’t acknowledge, weren’t anticipating, or have been despatched from a questionable supply.
Phishing scams typically ship you issues to click on on that acquire info within the background, or direct you someplace else the place they’ll attempt to collect it from you willingly. With the prevalence of those sorts of assaults on the rise, assume twice earlier than interacting with something you’re despatched digitally.
Take into account Your Browser
Many people simply default to the browser that got here put in on our gadgets. Nevertheless, one other method to sidestep information breaches is to make use of a privacy-focused browser. Firefox is a well-liked choice that’s recognized for minimal information assortment. Different choices embody Courageous and DuckDuckGo.
Subsequent, remember to clear your shopping information usually, together with cookies, cached recordsdata, and saved permissions. And examine your permissions to show off entry to your location, digicam, and microphone. You’ll be able to flip them again on manually do you have to want them.
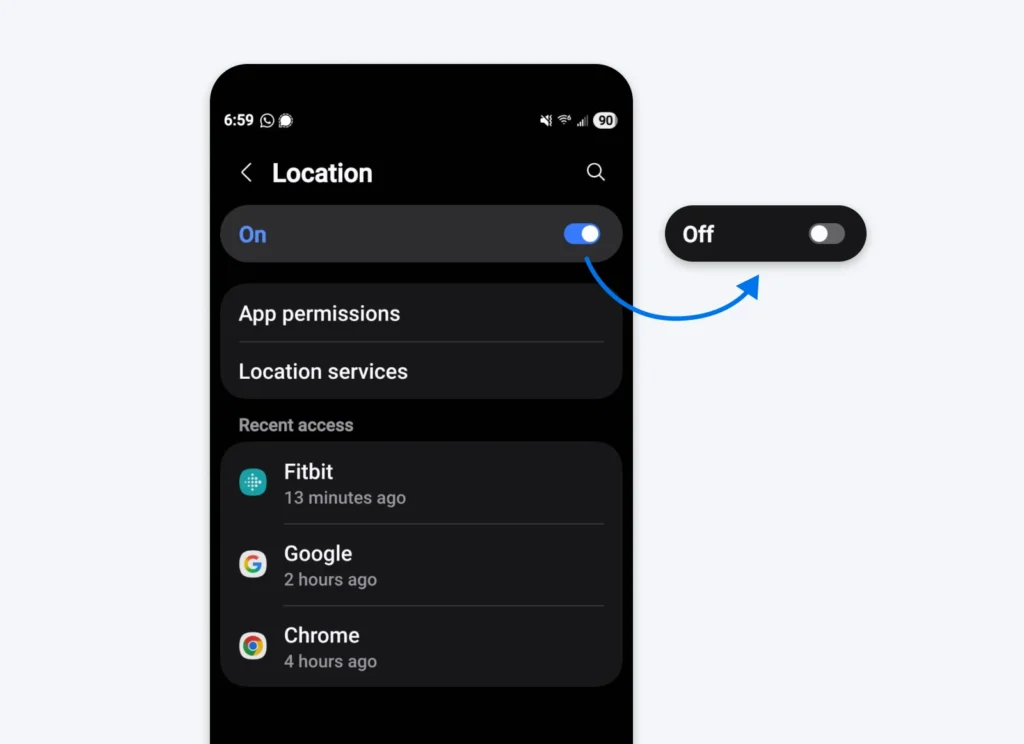
Cease Sharing Your Location In all places
Many cell apps share your location information immediately with third events or to auctions the place the knowledge will be purchased for promoting. If that wasn’t spooky sufficient, information brokers know this. They take part in these auctions and underbid simply to safe normal location info with out even paying for it.
Keep away from this by turning off location sharing on your whole gadgets and on every app you’ve downloaded. Once more, you may flip this again on selectively as wanted.
Go Darkish(er) On-line
Social media accounts are a serious supply of private information assortment. Modify your profile settings to remain as non-public as you may, and bear in mind that any info you select to share might fall into unknown fingers.
Keep away from partaking with messages from individuals you don’t know or belief. And don’t be afraid to make use of these block and report buttons if one thing feels fishy!
Cease Monitoring in Its Tracks
Most web sites use hidden monitoring codes (aka cookies) that acquire information about your exercise. Blocking these cookies can forestall your info from ending up with advertisers, information brokers, and scammers.
This information will get you began on blocking cookies on a number of the hottest browsers.
You too can increase safety with privacy-focused browser extensions that block trackers robotically. Some in style choices embody Privateness Badger and uBlock.
Scrub Your Info From the Web
Have you ever ever simply Googled your identify, or any identify,and been shocked in any respect the information you’ll find?
The websites that present up in these searches — for instance, Intelius, Spokeo, and BeenVerified — are all information brokers that acquire private info and make it means too straightforward for scammers and spammers to entry.
Fortunately, you may submit opt-out requests to cut back your visibility on these websites. However don’t overlook to examine again periodically. Your information will be added to those sources once more as they frequently scrape the net to compile profiles on people.
Try the hilariously-named Huge Ass Knowledge Dealer Choose-Out Listing to prioritize the way you sort out this challenge.
Clear Up Your Apps and Accounts
This one’s easy: Delete apps and accounts you not use. Deserted accounts that nobody is checking on and unfinished safety updates are prime targets for hackers.
To establish long-forgotten profiles, take a look at what you could have saved in your password supervisor. You too can search your electronic mail inbox for phrases like “new account,” “new password,” or “welcome,” to search out outdated or forgotten accounts.
Keep in mind, deleting an app out of your cellphone or laptop doesn’t normally delete your account! Go the additional mile and clear up these accounts to cut back the quantity of private info that’s floating round on the market simply ready to get scooped up.
Don’t Overlook Different Related Gadgets
Lastly, gaming consoles, sensible audio system, and even dwelling home equipment like your fridge can acquire delicate information in the event that they’re linked to the web.
Evaluate the privateness settings on the entire above gadgets in your house, and restrict pointless information sharing and assortment.
What To Do When Your Knowledge Will get Compromised
As we speak, information breaches aren’t a matter of if — they’re just about a matter of when.
Understanding how you can reply shortly by following the following pointers can shield your funds, id, and digital life.
Assess the Precise Danger
Step one is knowing what info was uncovered. Not all breaches are equally harmful.
For instance, if solely your identify and electronic mail have been stolen, you would possibly simply see extra spam.
But when delicate information like your social safety quantity or monetary establishment login have been compromised, the danger of id theft and fraud skyrockets.
Notifications from corporations typically let you know precisely what was affected. You should use that info to determine how lots of the following suggestions you need to do.
Set Up Fraud Alerts on Your Credit score
You’ll be able to request a fraud alert from any of the three main credit score bureaus (Experian, TransUnion, and Equifax).
This alert warns lenders that you could be be a sufferer of id theft, so they need to take additional steps to verify you might be who you say you might be earlier than approving any credit score in your identify.
Whenever you activate an alert with one bureau, it helpfully robotically applies to all three. Customary alerts final one 12 months, with the choice to resume.
Freeze Your Credit score
Freezing your credit score studies individually at every credit score bureau stops anybody from accessing your credit score file to open new accounts.
Whereas a freeze supplies glorious safety, it could, in fact, complicate reliable credit score purposes. If you could do one thing like apply for a mortgage or open a bank card throughout this time, you may briefly carry the freeze.
Rent a Knowledge Removing Service
Specialised providers can search the darkish internet for stolen private info and try and take away it. The darkish internet is decentralized and nameless, making guide elimination almost unattainable for most individuals — therefore why paid providers like this exist.
Whereas these providers aren’t excellent, they will considerably scale back the quantity of private info you could have floating round on the market, lowering your threat of fraud or phishing.
A few of these providers focus solely on the common internet or information brokers, so be sure to select one which covers the darkish internet if the delicate or worthwhile info has been compromised.
Attraction to Above-Board Knowledge Brokers
Outdoors the darkish internet, your info is most frequently in danger when it’s collected and offered by information brokers.
You’ll be able to personally submit requests to those brokers to delete and never promote your information, or you should use a specialised information elimination service to assist deal with it.
Compliance together with your request will depend upon the native legal guidelines of the information dealer, however this step can nonetheless restrict your information’s publicity and make it more durable for scammers to entry your info.
This text covers some good selections for information elimination suppliers that scan the darkish internet, information brokers, and past.
Watch Your Cost Apps Intently
Digital fee apps like Money App, Venmo, and Zelle typically have weaker safety than banks and bank card corporations do. So in case your information has been accessed wherever, many criminals will make a beeline to those platforms to see if they will break in.
Maintain an eye fixed out for any nefarious use by enabling transaction alerts so that you’re notified instantly of all exercise.
Report unauthorized transactions as quickly as doable. Scammers often take a look at whether or not or not you’re paying consideration by making actually small transactions at first. Should you catch fraudulent spending shortly, many fee platforms will even reimburse you.
Moreover, make certain 2FA and different out there safety measures are turned on inside these apps.
Replace All Your Passwords
After a knowledge breach, some of the essential steps is to vary your passwords.
Some individuals would advocate solely updating the affected accounts, however we’d argue it is a good time to replace all the pieces — particularly in case you’ve reused passwords. If hackers acquire entry to only one account, they typically strive the identical credentials on others.
Now could be the time to create sturdy, distinctive passwords for each on-line account. Completely keep away from utilizing the identical or comparable passwords throughout a number of websites.
Frightened you received’t be capable of keep in mind all of them? Think about using a password supervisor to generate and retailer complicated passwords securely. Then, all it’s important to do is keep in mind how you can log into that one web site.
Should you don’t know the place to start out, focus first on accounts which might be wealthy with delicate info, like electronic mail and banking.
Keep Sharp!
After a knowledge breach, hackers typically use the knowledge to launch focused phishing assaults.
They will impersonate reliable sources equivalent to your financial institution, authorities companies, and even associates to trick you into sharing extra delicate information.
Look ahead to these frequent indicators of phishing:
- Pressing messages pressuring you to behave instantly
- E mail addresses and language that appears uncommon, even when it’s simply barely off
- Sudden attachments
- Requests for delicate info or particulars that the requester ought to have already got, like account numbers, addresses, and names

FAQs About Knowledge Breaches
What’s a knowledge breach?
An information breach happens when unauthorized events acquire entry to delicate info, equivalent to passwords, monetary information, or private particulars.
How do I do know if I’ve been affected by a knowledge breach?
Count on a notification if an organization discovers that your info was collected in a current cyber assault. Nevertheless, this isn’t a failsafe. Your information might nonetheless be compromised with out your information.
What private info is most in danger in a knowledge breach?
Generally focused info contains passwords, social safety numbers, bank card information, medical data, and behavioral information like shopping and buying historical past.
What ought to I do instantly after a knowledge breach?
Assess the kind of information uncovered to grasp how fastidiously you could clear up, replace passwords, allow 2FA, arrange fraud alerts and/or credit score freezes, think about information elimination providers, and constantly monitor accounts for suspicious exercise.
Keep Secure Out There
Knowledge breaches are inevitable in at the moment’s digital world, however that doesn’t imply you’re powerless.
By understanding what private info faces safety dangers and taking proactive steps — like controlling your on-line footprint, utilizing sturdy safety practices, and responding shortly after a breach — you may scale back your publicity and shield your self from the worst penalties.
Did you get pleasure from this text?









